Cracking OTP Login with otplib: A Step-by-Step Guide
Learn to bypass OTP logins using otplib with simple steps and practical examples.

In the realm of cybersecurity, the battle against unauthorized access to digital platforms is ongoing. One of the key weapons in this arsenal is the One-Time Password (OTP) system. OTPs offer an additional layer of security by requiring users to input a unique code generated for each login attempt. However, while crucial for safeguarding sensitive data, OTPs also pose a challenge for test automation. In this guide, we'll delve into the world of OTPs, explore their significance, and demonstrate how to seamlessly automate OTP login testing using Playwright in conjunction with the otplib library.
OTP, as the name suggests, is a password that is valid for only one login session or transaction. It serves as a temporary authentication method, adding an extra layer of security beyond traditional username/password combinations. OTPs are widely used in various scenarios, including online banking, two-factor authentication (2FA), and user registration processes.
These OTPs are generated based on the current time and a shared secret key. They typically expire after a short period, usually 30 seconds to a few minutes.
Unlike TOTP, HOTP OTPs are not time-dependent. They are generated based on a counter value and a shared secret key, making them suitable for scenarios where real-time synchronization might be challenging.
Automating OTP login scenarios poses several challenges for testers. OTPs are time-sensitive and unique to each session, making it difficult to predict or hard-code them into test scripts. Additionally, the dynamic nature of OTPs requires automation frameworks to interact with external OTP generation services, further complicating the testing process.
To overcome the complexities of OTP testing, we turn to otplib, a versatile library designed for OTP generation and validation. This library simplifies OTP handling by providing intuitive APIs for generating and verifying OTPs, making it an ideal companion for any test automation framework.
Now, let's dive into the practical aspect of automating OTP login testing using Playwright and otplib. We'll walk through the steps of setting up our automation environment, creating OTP automation scripts, and executing tests seamlessly.
Before we begin, ensure you have Node.js installed on your system, since otplib is a JS library.
Inside your test automation framework, you can install it with:
npm i -D otplibNow you can create a generate-otp-pass.js:
const { authenticator } = require("otplib");
const secret = "YOUR-SECRET-KEY";
const token = authenticator.generate(secret);
console.log("6 digit token: ", token);
try {
const isValid = authenticator.check(token, secret);
console.log("Token valid: ", isValid);
} catch (err) {
console.error(err);
}Explanation:
- We import
authenticatorfrom the otplib, since we will setup 2FA on Google Account using the Google Authenticator. - We need to provide
secret. To obtain the secret, follow the steps outlined below. - We check if the generated 6 digit token is valid, so we can be sure that we can use it for the login form.
- Go to your Google Account Settings, then go to
Securityand select theAuthenticator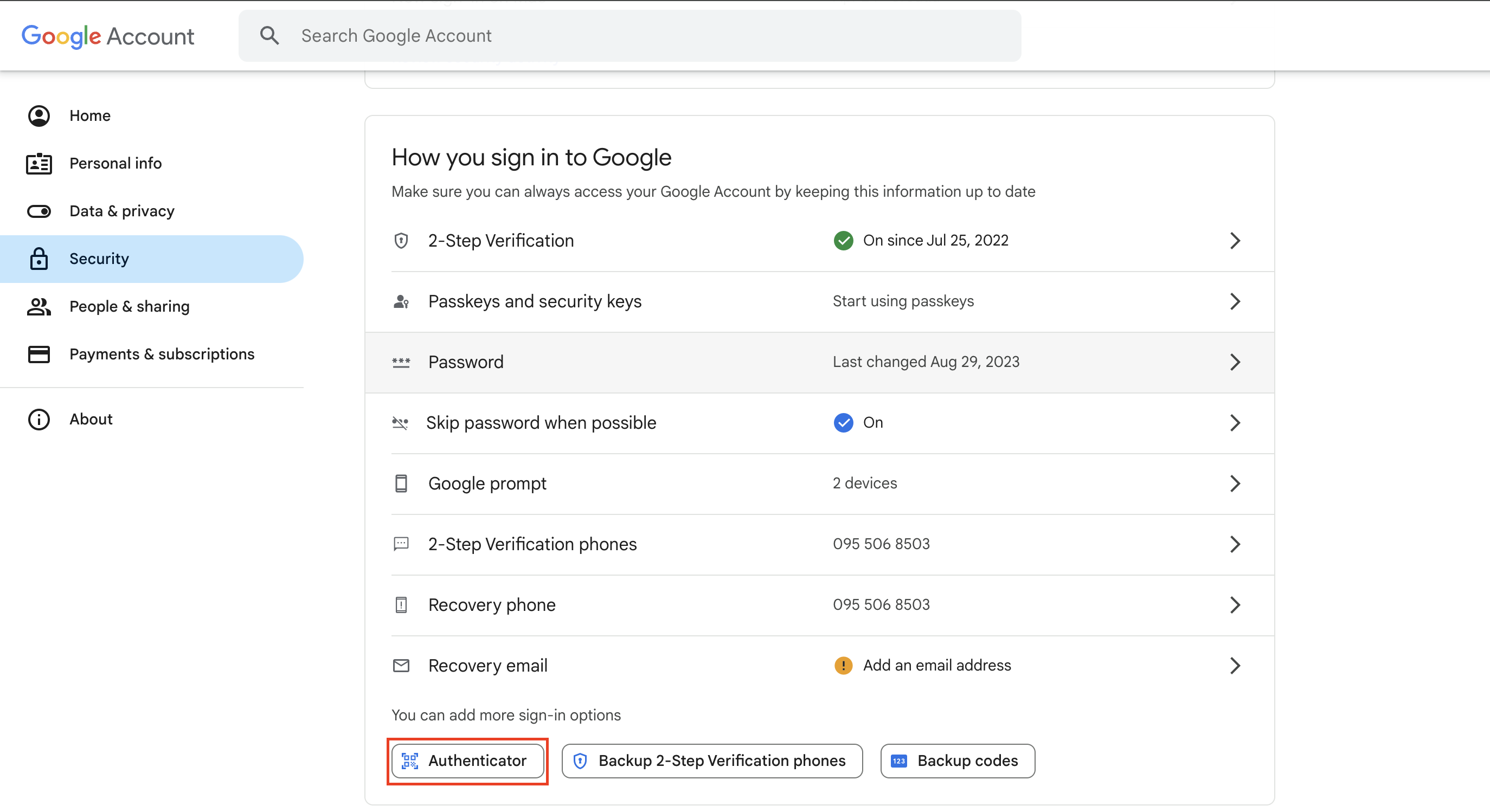
- Click on the
Set the authenticatorbutton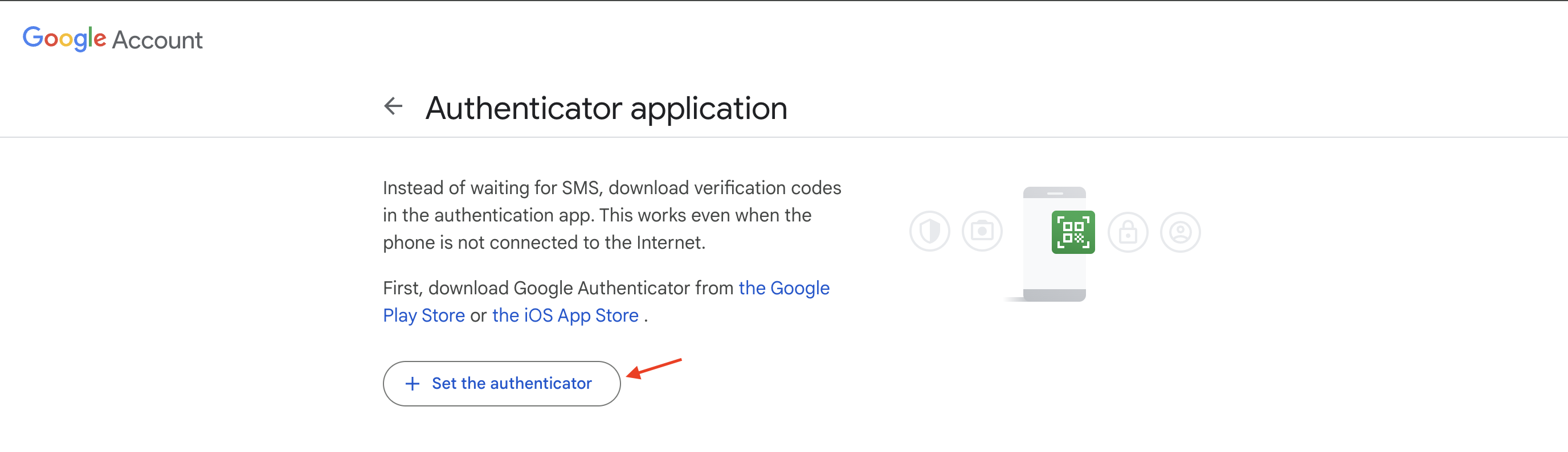
- Click on the
Can't scan it?text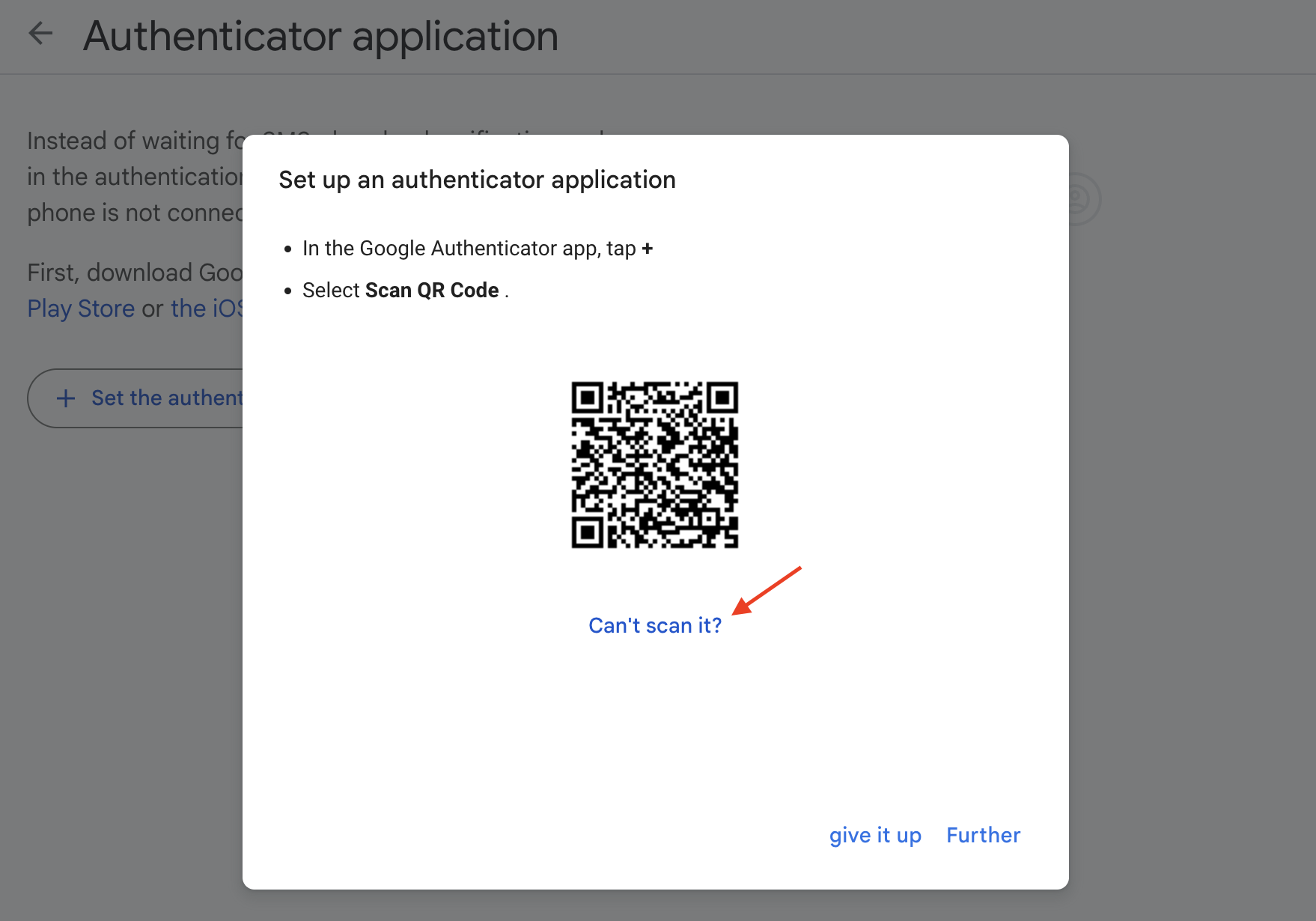
- Add the provided key to the Google Authenticator app on your phone and save it.
Also, replace
YOUR-SECRET-KEYwith ths key within the script.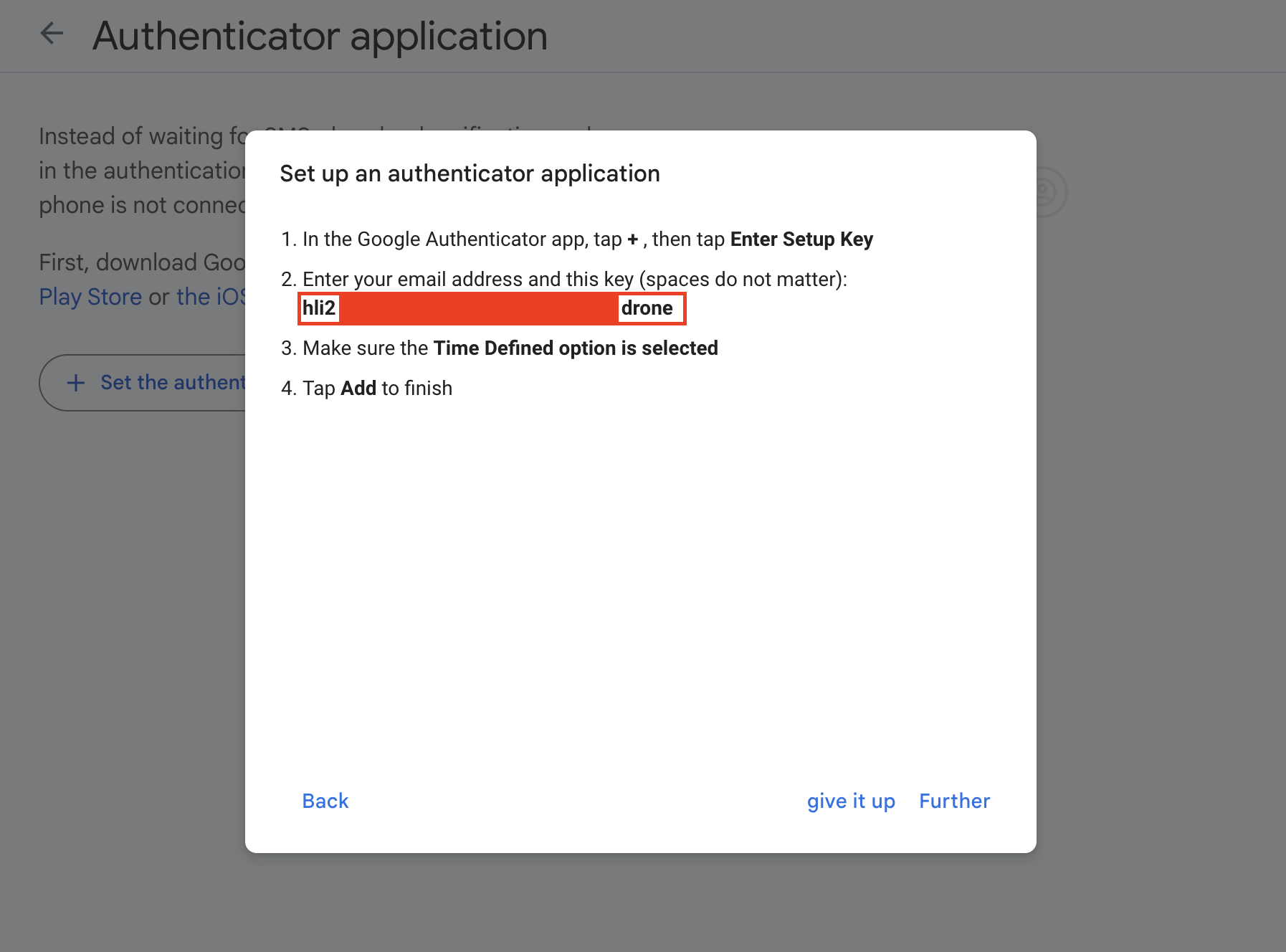
Once you are ready, you can run the file with:
node generate-otp-pass.jsIf everything was set up correctly, the output should be like this:
6 digit token: 020790
Token valid: trueSo, now we know how to get the 6 digit token. You can use the logic and even create a function that you will run to fill in the form before the log in.
Also, keep in mind that it is always better to export secrets as environment variables, and avoid hardcoding them in the scripts.
In conclusion, automating OTP login testing is an essential aspect of ensuring the security and usability of applications that rely on two-factor authentication.
By leveraging otplib, you can effectively streamline the process of generating and validating OTPs, regardless of the test automation framework you use. The steps and examples provided in this guide equip you with the knowledge to integrate OTP testing seamlessly into your chosen framework, be it Playwright, Selenium, Cypress, or any other.
Additionally, this approach can be extended to create 2FA for various platforms, including Google, Microsoft, and more. Embracing these practices will help you deliver secure, reliable, and user-friendly applications, ultimately enhancing the overall quality and robustness of your software.

